HTTPS (Hypertext Transfer Protocol Secure)
HTTPS or as Hypertext Transfer Protocol Secure, being the HTTP extension with crypto operation capabilities is a secure channel used in the network for data transfer. Developed by the Netscape Communications Corporations in 2000 aiming to providing identity verification and secured communications. The need for SSL came after the introduction of few sniffer programs which allow grabbing all of the computer traffic through a network (mainly Internet),it may be e-mails, passwords, payment details or crucial data that can be hunted. When the data is Encrypted it becomes impossible for them to know what the data is about, but still there won’t be much trouble to get the traffic data. This made banks, email service provides and other site transfering personal informations to switch to connection based on HTTPS. Currently HTTPS is supported by the almost all browsers.
HTTPS
In fact, HTTPS is not a separate protocol, but a common HTTP operating via SSL (Secure Socket Layer) and TLS (Transport Layer Security) encryption mechanisms. The HTTPS protocol used for sending messages provides authentication validation of those users, who seek access to message queue via web-server as well as allows setting up the secured connection between a sender and a receiver. A sender is regarded as a SSL client, and a receiver as SSL server. It should be noted that authentication validation at SSL session setup does not check with message authentication to prove the correctness of message and the sender’s identity.
In order to make a web-server to process HTTPS, it is required to set up a certificate for that web-server. HTTPS authentication uses two types of certificates, as provided by the Certificate Authority:
- Server certificates. These are the keys created by means of encryption. They are the ciphered text elements used to ensure secure connection among the group of users.
- Client certificates. The personal information regarding a user is stated in these certificated ensuring the identification of a SSL client to a server.
It’s possible to apply your own certificates without referring to the Certificate Authority. They are called the self-signed certificates and considered to be less reliable compared to server and client ones.
Service Side
Before setting up a SSL connection with a client a server certificate is to be provide to the client in order to get started. A server certificate, can be issued on the name of NetBIOS or DNS name by a Certification Authority. The server certificate, containing the Certification Authority signature, the public key of a sender, some supplemental information about a receiver and a validity date, should be received from a Certification Authority which guarantees that the certificate owner is verified.
Each certificate contains two keys: a public and a private. The public key is used for traffic encryption, and the private key is used for de-encrypting the traffic received from the client. In order to perform the authentication validity, it is necessary to prove two-way trust relationship by means of a signed certificate.
Client
With every this done at the server next part is to be with the client. The client certificate is provided by the Certificate Authority. In general, client certificates mapping is a basis of authentication validation. If all conditions set by server is met, a sender (SSL client) and a receiver (SSL server) create and exchange SSL session keys.
SSL and TLS
SSL (Secure Sockets Layer) is a cryptographic protocol providing the secure connection between a client and a server. SSL, initially developed by the Netscape Communication Corporation. Thereafter, the RFC standard, called TLS, was generated and accepted on the basis of SSL 3.0. THis protocol ensures data exchange privacy between a client and a server, which assigns TCP/IP (The Internet Protocol) with a public key asymmetric algorithm used for encryption process.Hence, if one key is used for encryption, consequently, the another one is required for decryption.
The SSL protocol consists of two sub protocols, i.e. a SSL Record protocol and a SSL Handshake protocol. The former one defines a data transmission format. The SSL protocol includes a handshake with SSL Record protocol to provide message series exchange between a server and a client at first connection. The SSL protocol constitutes a secure channel with three basic features:
- Secure – All Messages are Encrypted.
- Authenticated – Authentication is must on server part where as its optional on Client side.
- reliable.
SSL not only provides data safety in the World Wide Web, but also performs server and client authentication.
The main objectives of the SSL protocol are:
- Cryptographic security – It provides a secure path to share information remotely providing no chance for any third-party interference.
- Consistency – Compactable with any platform.
- Expandability – New methods can be implemented easily.
- Efficiency – It can efficiently transfer data over an open channel b/w two users or server and user
The SSL protocol supports three types of authentication validation: client and server authentication, server authentication with unauthenticated client, and full anonymity.A completely anonymous session is, actually, open to attacks.
The TLS (Transport Layer Security) protocol was developed on the basis of SSL 3.0 specification by the Netscape Company. The main function of it is in providing safety and data integrity between two communicating applications. The basic tasks of TLS are identical to those of SSLv3.
Two layers of TLS : the Record Protocol and the Handshake Protocol. The First one is based on connection confidentiality and integrity, used for encapsulating higher level protocols. The Handshake protocol allows a server and a client uthenticating each other.
Note:TLS 1.0 and SSL 3.0 are incompatible.Despite all difference both protocols pursue the same goal that is secure data transfer in the net.
Digital Certificates
The simplified classification of Digital Certificates consists of:
- Domain-validated certificates.
- Extended-validated certificates.
- Organization-validated certificates.
- Wildcard SSL
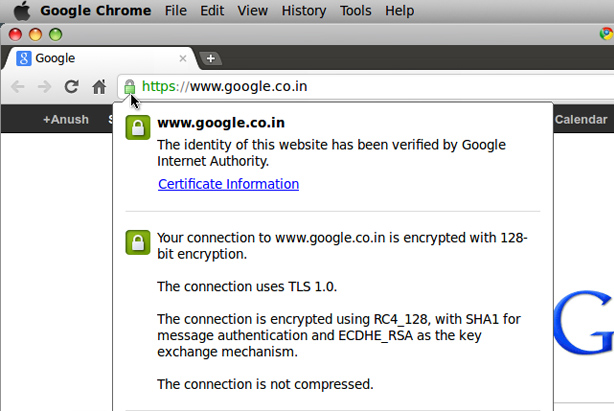
Domain-validated certificates
Domain-validated certificates come with the advantage of being issued almost immediately and without the need to submit company paperwork. This makes DomainSSL ideal for businesses needing a low cost SSL quickly and without the effort of submitting company documents.
Domain-validated certificates offers Low assurance, Because the company is not validated, these certificates don’t help your visitors know who is running the site. If you have an e-commerce site, your potential buyers may be scared off.
Domain validated certificates do almost nothing to verify that you are talking to who you think you are talking to.
It can be used only in situations where there is’t any need to assure visitors or where there is little chance for third-party attack
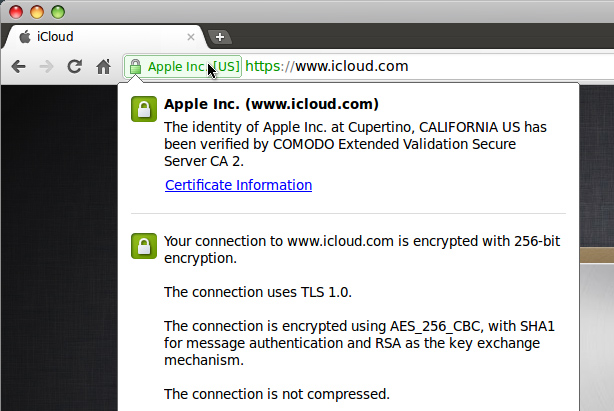
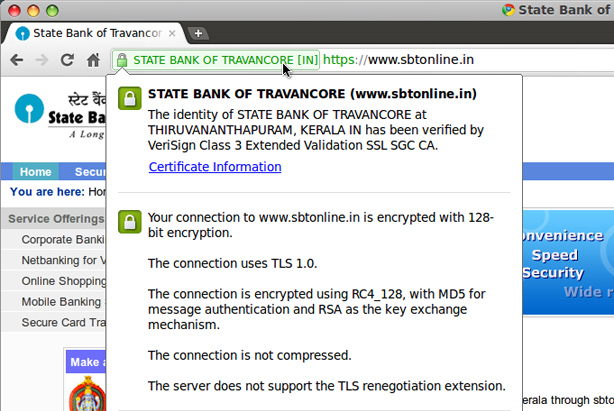
Extended validated certificates(EV)
An Extended validated certificates is a new type of certificate that is designed to prevent phishing attacks better than normal SSL certificates. Since An SSL Certificate Provider has to do some extensive validation to give one, it makes it Extended validated certificates so special. The following Verification has to be done:
- Verifying that the organization is legally registered and active.
- Verifying the address and phone number of the organization.
- Verifying that the organization has exclusive right to use the domain specified in the EV SSL Certificate.
- Verifying that the person ordering the certificate has been authorized by the organization.
- Verifying that the organization is not blacklists by any government.
The above mentioned standards followed by all SSL providers was created and agreed upon by all the members of the CA/Browser Forum. To know what an SSL provide must follow check out the EV SSL Certificate Guidelines.
The complete information of the organization is displayed in the Certificate.
Organization validated certificates
They require validation of the official title and the domain name of the organization. The Certification Authority checks the official title by requesting copies of paper documents, for instance, a founders agreement.
Organization validated certificates key features include:
- Contains your authenticated organization details
- 2048 bit future proof SSL Certificates
- A single certificate secures both www.domain.com and domain.com
- Universally works with all browsers, mobile phones and devices
- Optional SGC technology increases weak encryption strength in older browsers
- Reissue as many times as needed during the validity period
All Organization validated certificates requires domain validation as well supplying business documents for business authentication. Organization validated or Business validation is the manual process and commissioned by certificate authorities only. It takes around two to three business days accomplishing the whole validation process and then only the SSL would be issued after successful authentication.
The standard HTTP is changed to HTTPS, automatically telling the browser that the connection between server and client is Secure.
Organization validated or Business validation SSLs are highly recommended for the online shopping cart websites having physically registered business. All Organization validated or Business validation SSL supplies your real business name and locality as well contact information in SSL properties. Organization validated or Business validation SSL gains more customer trust than domain validation SSL and helps you gathering more business compare to domain validation SSL installed website.
Wildcard SSL
A typical standard SSL Certificate can only be issued to a single Fully Qualified Domain Name, i.e it can be applied exactly to domain to which it has been issued. With the Wildcard SSL option activated you can expand what’s possible by receiving an SSL Certificate issued to *.domain.com.
The * character allows the Certificate to be used on an unlimited number of subdomains across an unlimited number of servers, all for the same one-time cost even if you plan to add more in the future.
If you configure *.coolexample.com, you can secure
www.coolexample.com
photos.coolexample.com
blog.coolexample.com, etc.
If you configure *.www.coolexample.com, you can secure
mail.www.coolexample.com
photos.www.coolexample.com
blog.www.coolexample.com, etc.
A Wildcard SSL secures only the level of subdomain you specify,i.e. if a certificate is issued for *.www.coolexample.com, it will not secure www.coolexample.com. It is recommended to use any of the version and make a 301 permenant redirect from NON WWW version to WWW version
It should be mentioned that the major Certification Authorities are VeriSign, RapidSSL, Thawte, GeoTrust, StartCom, Comodo, and GlobalSign. But there are hundreds of root and mediatory authorities, so that it is very difficult to define which one is trustworthy and which one is not.Currently there are some ways to break HTTPS (inclusive of SSL and TSL protocols) that can create really catastrophic problems for the victim.